BackdoorCTF 2023
Web/Beginner/Secret_of_jackal
Challenge Overview
Description: I left a message for you. You will love it definitely
Author: j4ck4l :>)

We have been given a website. It’s a simple lfi challenge
Hmm so to understand the functionality more let’s see the source code
1 | def ignore_it(file_param): |
Vulnerability Identification
Okay so let’s analyse it block by block.
It’s a simple page which include local files. So if you try to read flag file which is one directory back as given in the Dockerfile it will give you a message which says "Illegal characters detected in file parameter!"
So if we see the code the useless() first sanatise the output using ignore_it() function and will remove the / & . characters and then url decodes it using another_useless_function
Exploiting the Vulnerability
If you execute this code locally if you encode the file path 2 times it should give you the flag but it will not run on the server.
Because chrome already decodes the url 1 time and then 2 times it will be done by our code so in total 3 times we have to encode the file path.
So our final payload is %25252E%25252E%25252Fflag%25252Etxt
Obtaining the Flag
So after giving the payload you will get the flag
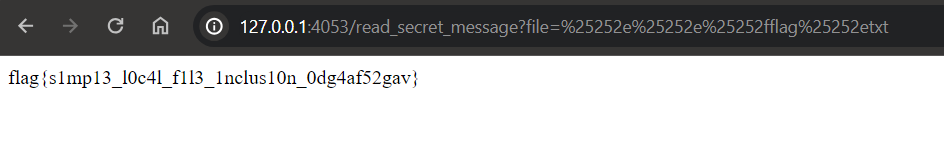
Flag: flag{s1mp13_l0c4l_f1l3_1nclus10n_0dg4af52gav}
Web/php_sucks
Challenge Overview
Description: I hate PHP, and I know you hate PHP too. So, to irritate you, here is your PHP webapp. Go play with it.
Author: j4ck4l :>)
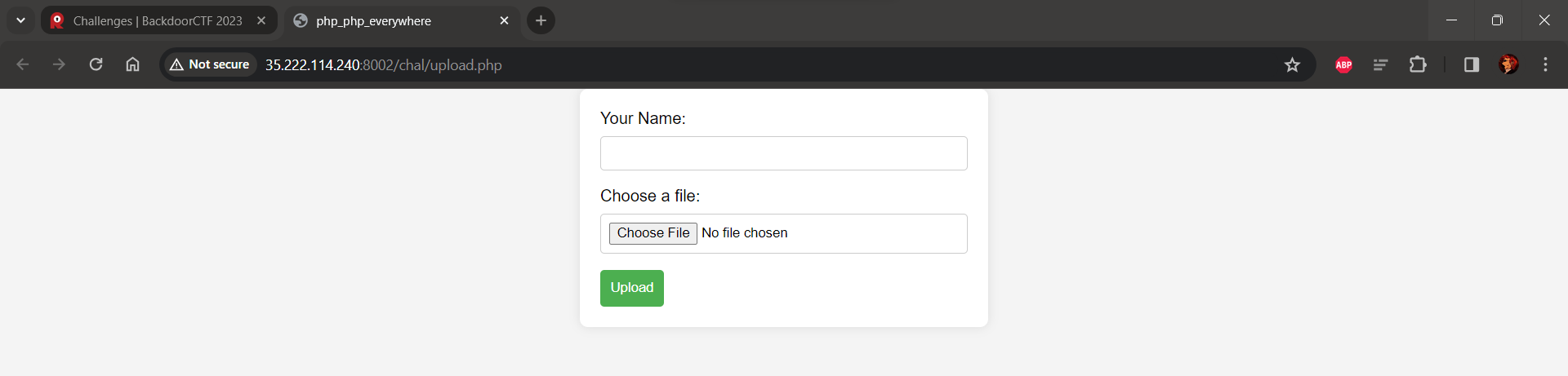
We have been given a website. We can see a simple upload form.
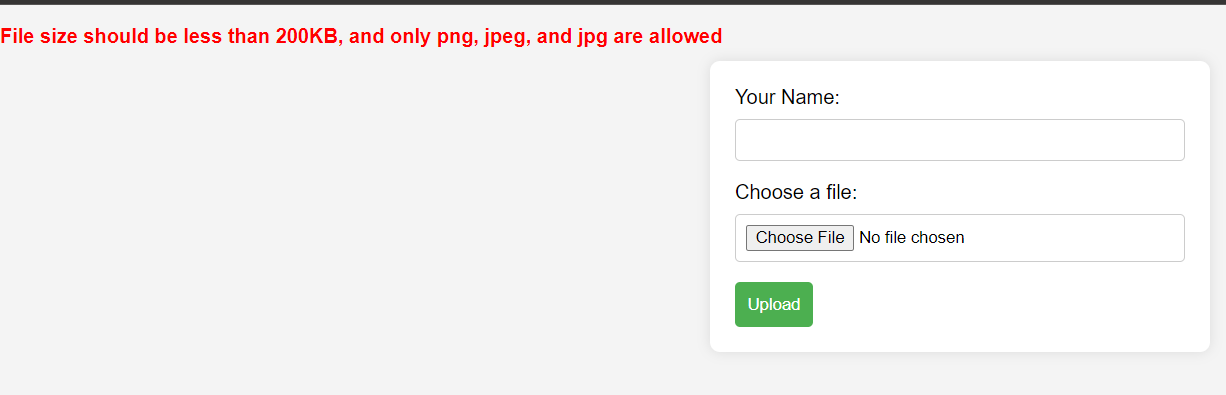
Let’s try to upload a text file. And the server responds with File size should be less than 200KB, and only png, jpeg, and jpg are alloweded
Hmm so to understand the functionality more let’s see the source code
The code is obfuscated and in a single line, let’s use an online beautifier and we get the below source code
1 |
|
Vulnerability Identification
Okay so let’s analyse it block by block.
It first asks for a file and then it checks the file extension using
1 | $fileExt = strtolower(pathinfo($fileName, PATHINFO_EXTENSION)); |
so if the extension is jpg, jpeg, png and the file size is less than 200kb it will try to execute further instructions.
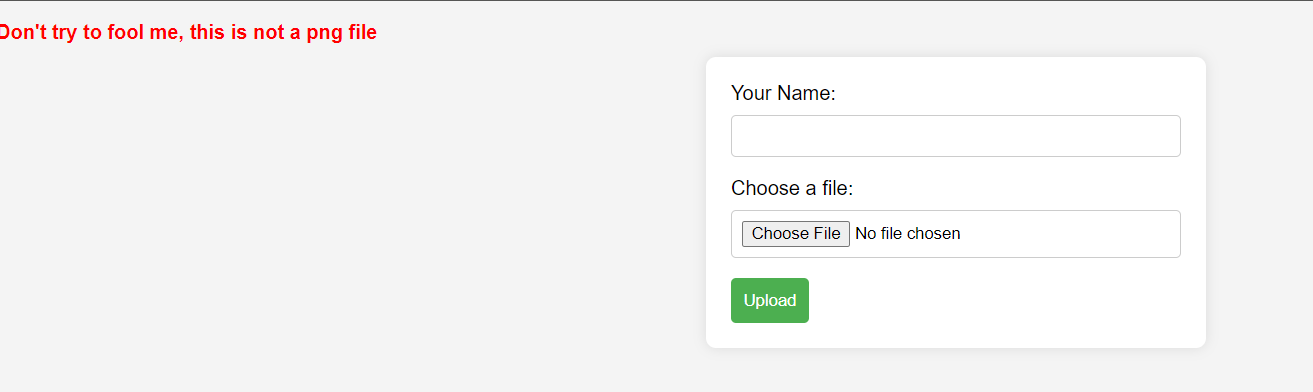
Okay then if you pass the extension check we have another check that is the MIME type check. So if you try to fool the server by uploading a file like exploit.php.png but the file type is actually a php then the server will give you and error –> Don't try to fool me, this is not a png file.
Okay so let’s try to upload a file with the header png/jpeg/jpg
We can do it with a file using xxd -r -p -o 0 <(echo 8950 4e47 0d0a 1a0a 0000 000d 4948 4452) exploit.php.png
So if you check the file type now it will bypass the MIME check.
But the problem is if it is uploaded it will be uploaded as exploit.php.png so an image will open so it is not helpful to solve the challenge
Exploiting the Vulnerability
So to exploit this we will set the header of the file to PNG. And then we will inject some php code to exploit the server.
We will name this file as exploit.php%00.png. The nullbyte will bypass the checks performed and the name of the file which will be uploaded on the server will be exploit.php as it will ignore the part after the nullbyte.
But here is a twist.
Have a look at this line of code
1 | $fileName = strtok($fileName, chr(7841151584512418084)); |
if you use php interactive shell you can see the chr(7841151584512418084)
1 | php > echo chr(7841151584512418084); |
so the file name will be split by $.
So to exploit this we will create a file exploit.php%24.png or exploit.php$.png with header of png and content as
1 | �PNG |
Obtaining the Flag
So we will upload the file and the file name which will be uploaded will be exploit.php and when we open the file . BOOM we got the shell
let’s do rce now and list the files two directories back we get the name of flag file as s0_7h15_15_7h3_fl496_y0u_ar3_54rch1n9_f0r.txt
and now cat ../../s0_7h15_15_7h3_fl496_y0u_ar3_54rch1n9_f0r.txt to read the file.
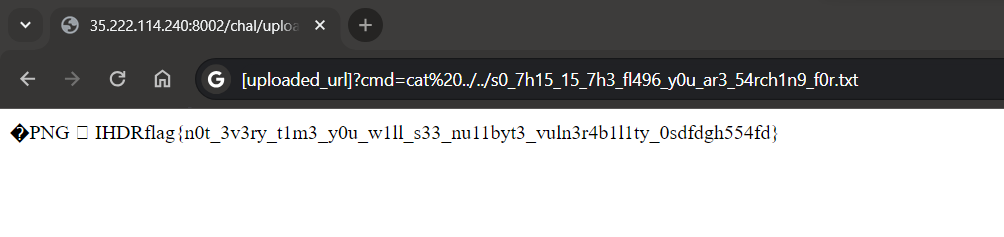
Flag: flag{n0t_3v3ry_t1m3_y0u_w1ll_s33_nu11byt3_vuln3r4b1l1ty_0sdfdgh554fd}
Thank You